Last updated: 22nd February 2022
Advisory publication date: 13th December 2021
Latest update
With our latest round of product releases, we address all vulnerabilities disclosed in this advisory. For each supported CloverDX minor version we provide a maintenance release that includes the latest version Log4j.
Following table provides a quick overview of minimal product versions that address all vulnerabilities disclosed in the advisory:
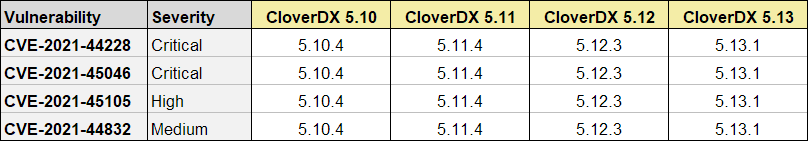
Every product version delivered after the versions mentioned in the table above will also address the vulnerabilities disclosed in this advisory.
Summary
This advisory discloses four vulnerabilities in Log4j library and provides overview of their impact on CloverDX products. These vulnerabilities impact all versions, starting with CloverDX 5.2.0. See complete overview in section Affected product versions below.
It was also found that a hot-patch released for Amazon Corretto JDK causes CloverDX Server to crash on startup. This does not affect companies using AWS Marketplace offers as these do not ship with Amazon Corretto JDK but may affect companies with custom deployments on AWS EC2. Please read a note at the end of this advisory.
Log4j library is used in all CloverDX products to manage logs. Vulnerabilities disclosed in this advisory can lead to remote code execution (RCE) or denial of service (DOS) attacks against CloverDX.
CVE IDs
- CVE-2021-44228
- CVE-2021-45046
- CVE-2021-45105
- CVE-2021-44832
Affected product versions
- CloverDX 5.13.0
- CloverDX 5.12.x before 5.12.3
- CloverDX 5.11.x before 5.11.4
- CloverDX 5.10.x before 5.10.4
- CloverDX 5.9.x (this version is retired and does not receive security fixes)
- CloverDX 5.8.x (this version is retired and does not receive security fixes)
- CloverDX 5.7.x (this version is retired and does not receive security fixes)
- CloverDX 5.6.x (this version is retired and does not receive security fixes)
- CloverDX 5.2.x to CloverDX 5.5.x (these versions are EOL and do not receive any support or bug fixes)
- CloverDX releases before CloverDX 5.2.0 and all CloverETL releases are not affected since they use older version of Log4j (version 1.x). However, Log4j 1.x is no longer supported and contains various security vulnerabilities – like for example CVE-2021-4104 – which may allow similar kind of attack.
Fixed product versions
- CloverDX 5.13.2 and 5.13.1 – these releases contain latest Log4j version and are the safest releases. You should upgrade to 5.13.2 if possible.
- CloverDX 5.12.3 – released on 22nd February, this release addresses all vulnerabilities from this advisory.
- CloverDX 5.11.4 – released on 22nd February, this release addresses all vulnerabilities from this advisory.
- CloverDX 5.10.4 – released on 8th February 2022. This release contains latest version of Log4j which addresses all vulnerabilities mentioned in this advisory.
CVE-2021-44228: RCE vulnerability in Log4j (Log4Shell)
Apache Log4j2 <=2.14.1 JNDI features used in configuration, log messages, and parameters do not protect against attacker-controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled.
All supported versions of CloverDX use Log4j version 2.11.1 and will be updated to the latest Log4j version 2.15.0.
- Log4j acknowledgement and details: https://logging.apache.org/log4j/2.x/security.html
- CVE details: CVE-2021-44228 (NVD record)
- CVSS 3.1 score: 10.0 (critical)
- CVSS 3.1 vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
- CloverDX Bug Tracker: CLO-22450: Log4Shell: Upgrade Log4j to 2.15.0
CVE-2021-45046: Thread Context Lookup Pattern vulnerable to RCE in certain non-default configurations
It was found that the fix to address CVE-2021-44228 in Apache Log4j 2.15.0 was incomplete in certain non-default configurations.
When the logging configuration uses a non-default Pattern Layout with a Context Lookup (for example, $${ctx:loginId}), attackers with control over Thread Context Map (MDC) input data can craft malicious input data using a JNDI Lookup pattern, resulting in an information leak and remote code execution in some environments and local code execution in all environments; remote code execution has been demonstrated on macOS but no other tested environments.
- Log4j acknowledgement and details: https://logging.apache.org/log4j/2.x/security.html
- CVE details: CVE-2021-45046 (NVD record)
- CVSS 3.1 score: 9.0 (critical)
- CVSS 3.1 vector: CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:H
- CloverDX Bug Tracker: CLO-22463: Upgrade Log4j to 2.16.0
CVE-2021-45105: Uncontrolled recursion of self-referential lookups
Apache Log4j2 versions 2.0-alpha1 through 2.16.0 did not protect from uncontrolled recursion from self-referential lookups.
When the logging configuration uses a non-default Pattern Layout with a Context Lookup (for example, $${ctx:loginId}), attackers with control over Thread Context Map (MDC) input data can craft malicious input data that contains a recursive lookup, resulting in a StackOverflowError that will terminate the process. This is also known as a DOS (Denial of Service) attack.
- Log4j acknowledgement and details: https://logging.apache.org/log4j/2.x/security.html
- CVE details: CVE-2021-45105 (NVD record)
- CVSS 3.1 score: 7.5 (high)
- CVSS 3.1 vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
- CloverDX Bug Tracker: CLO-22482: Upgrade Log4j to 2.17.0
CVE-2021-44832: RCE via JDBC Appender when attacker controls Log4j configuration
Apache Log4j2 versions 2.0-beta7 through 2.17.0 (excluding security fix releases 2.3.2 and 2.12.4) are vulnerable to a remote code execution (RCE) attack where an attacker with permission to modify the logging configuration file can construct a malicious configuration using a JDBC Appender with a data source referencing a JNDI URI which can execute remote code. This issue is fixed by limiting JNDI data source names to the java protocol in Log4j2 versions 2.17.1, 2.12.4, and 2.3.2.
Note that CloverDX does not allow unauthenticated users to control Log4j configuration and therefore this issue is much harder to exploit in CloverDX since the attacker requires CloverDX access and permissions to modify configuration or write access to file system where CloverDX runs.
- Log4j acknowledgement and details: https://logging.apache.org/log4j/2.x/security.html
- CVE details: CVE-2021-44832 (NVD record)
- CVSS 3.1 score: 6.6 (medium)
- CVSS 3.1 vector: CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:U/C:H/I:H/A:H
- CloverDX Bug Tracker: CLO-22512: Upgrade Log4j to 2.17.1
Fix
As of 22nd February 2022, we recommend all customers to upgrade their CloverDX instances to CloverDX 5.13.2 which contains the latest version of Log4j library which addresses all vulnerabilities reported in this advisory.
If you are unable to update to CloverDX 5.13.2 and are running and older supported release, you can also upgrade to the latest maintenance release with the same minor version.
We will be monitoring the situation and will release additional fixes as necessary in compliance with our Security policy.
What you need to do
- 5.13 users – Upgrade to CloverDX 5.13.2.
- 5.12 users – Upgrade to CloverDX 5.13.2 (recommended) or to CloverDX 5.12.3 (easier upgrade).
- 5.11 users – Upgrade to CloverDX 5.13.2 (recommended) or CloverDX 5.11.4 (easier upgrade).
- 5.10 users – Upgrade to CloverDX 5.13.2 (recommended) or CloverDX 5.10.4. CloverDX 5.10.4 addresses all Log4j vulnerabilities and the upgrade is easier, however, 5.13.1 is more secure as it addresses many other unrelated issues as well.
- Older versions – We recommend you upgrade to CloverDX 5.13.2. If you cannot upgrade, apply all mitigation steps outlined below.
Regardless of the version you upgrade to, we recommend you review the mitigation steps listed below – especially if you changed default Log4j configuration for CloverDX. In default configuration with all fixes applied, CloverDX is not vulnerable to the vulnerabilities disclosed in this advisory.
Monitor this Security advisory in our knowledge base as we regularly update its contents with latest information on releases and other related announcements.
Mitigation
These mitigation steps are recommended by authors of Log4j Java library and re-written in the context of CloverDX installation.
CVE-2021-44228 and CVE-2021-45046 (Critical severity)
The only reliable way to mitigate JNDI lookup related vulnerabilities is to remove classes responsible for handling JNDI lookups. It is possible to completely remove the functionality from Log4j without negatively affecting CloverDX.
To remove the class, you will need to modify log4j-core-2.*.jar (version would differ based on CloverDX release) like so:
zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
Note that the library is present in CloverDX Server as well as in CloverDX Designer and therefore the steps must be repeated for each of them.
In CloverDX Server, the library can be found in your application server’s deployment directory. For Tomcat this will be in <Tomcat home>/webapps/clover/Web-inf/lib. For other application servers, please consult their user guide.
In CloverDX Designer, the library is located in <Designer root>/plugins/com.cloveretl.gui_VERSION/lib/lib directory. The VERSION depends on version of your Designer – for example, for CloverDX 5.12.0 the VERSION will be 5.12.0.11.
Important note: A previously suggested fix to disable JNDI lookups in logging messages by setting Java system property log4j2.formatMsgNoLookups to true was later proven insufficient.
CVE-2021-45105 (High severity)
CloverDX does not use Context Lookups internally, yet we still recommend checking for potential customizations that may have been done to Log4j configuration. Please refer to Log4j documentation to check if your deployment does not use any non-standard configuration.
According to this current recommendation, it is necessary to check configuration files to not include the following settings:
- In PatternLayout in the logging configuration, replace Context Lookups like ${ctx:loginId} or $${ctx:loginId} with Thread Context Map patterns (%X, %mdc, or %MDC).
- Otherwise, in the configuration, remove references to Context Lookups like ${ctx:loginId} or $${ctx:loginId} where they originate from sources external to the application such as HTTP headers or user input.
CVE-2021-44832 (Medium severity)
CloverDX does not use JDBC Appender and therefore this vulnerability does not impact CloverDX in its default configuration.
To ensure you are not impacted, review your Log4j configuration to verify that you did not enable JDBC Appender as part of you customization.
If you use JDBC Appender, disable it if possible. If you require JDBC Appender, make sure that it does not use any protocol other than Java.
Mitigation summary
All versions of CloverDX newer than CloverDX 5.2 use Log4j 2.x and therefore above mitigation steps are universally applicable.
If you are on older version of CloverDX (before 5.2) or are still using CloverETL, you are not affected by this issue since those versions use older Log4j which does not implement the JNDI lookup feature. However, Log4j 1.x is very old and is not secure either. It is affected by (for example) CVE-2021-4104 which allows for similar RCE attacks.
Support
If you did not receive this email directly and you want to receive Security Advisory emails like this in the future, subscribe to the CloverDX Security Alerts mailing list here
If you have any questions or concerns regarding this advisory, please raise a CloverCARE support request via Customer Portal.
References
Additional information
To verify whether you are affected by the original Log4Shell vulnerability, you can read our Tech Blog article How to verify if you are affected by Log4Shell vulnerability.
AWS EC2 deployments with Amazon Corretto
AWS published a hot-patch (https://github.com/corretto/hotpatch-for-apache-log4j2) for Log4Shell (CVE-2021-44228) and CVE-2021-45046 described in this advisory.
The patch, however, causes CloverDX Server to crash during startup. This patch is automatically installed with an update of java-*-amazon-corretto (e.g. by using yum update) and affects any other JVM installed on EC2 instance.
To prevent CloverDX Server from crashing on startup, we recommend uninstalling java-*-amazon-corretto and log4j-cve-2021-44228-hotpatch packages entirely from your EC2 instance. Instead, please install Java from any of the supported vendors and implement mitigation steps or upgrades as described in this advisory.
Update history
- 2022-02-22 – Updated information related to latest CloverDX 5.12.3 and 5.11.4 releases.
- 2022-02-15 – Updated information related to latest CloverDX 5.13.2 release.
- 2022-02-11 – Updated information related to latest CloverDX 5.10.4 release.
- 2022-01-12 – Updated information related to latest CloverDX 5.13.1 release.
- 2022-01-03 – Updated information related to new medium severity vulnerability (CVE-2021-44832). General text update for better readability and clarity.
- 2021-12-22 – Updated information related to latest 5.12.2 release.
- 2021-12-21 – Updated information about release 5.11.3 and latest findings using AWS’ Amazon Corretto JDK.
- 2021-12-20 – Added information about latest vulnerability, updated information about CVE-2021-45046 re-classified as Critical as it allows similar attack as the original Log4Shell. Updated recommendations and added detailed overview of released versions and which vulnerabilities they address. Added mitigation step for CVE-2021-45105.
- 2021-12-17 – CloverDX 5.10.3 release information added. Added information about second Log4j vulnerability (DOS) and updated mitigation steps and all other details to match the latest information available about the issue.
- 2021-12-14 – CloverDX 5.13.0 release information added. Updated supported versions list and added more details into "Fix" and "What you need to do" sections. Added "Additional information" section and a link to Tech Blog article.

Comments 0